Zscaler – Bypass Tamper Protection
| Title | Zscaler – Bypass Tamper Protection |
| Discovery date | 08/11/2021 |
| Release date | 04/11/2022 |
| Credits | Almaviva Cyber Defence Threat Center |
| Affected products | Zscaler Client Connector |
| Class | Bypass business logic |
Disclosure timeline
| 08/11/2021 | First report of vulnerability to zscaler |
| 11/10/2022 | Second report of vulnerability to zscaler |
| 04/11/2022 | Request for CVE ID (Not Assigned) |
| 10/11/2022 | JCV-2022.11.10.01 released |
Vulnerability details
This vulnerability allows the user to rename the system folders of the Zscaler Client Connector, bypassing the password request throughout the phase of the agent removal.
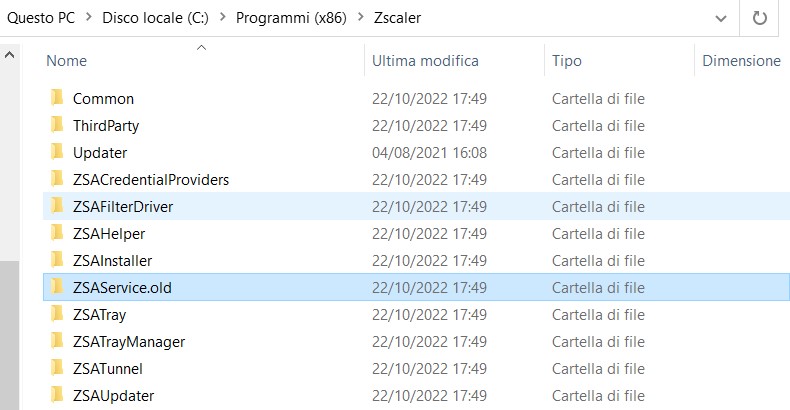
Inside the product’s folder, that by default is C:\Program Files (x86)\Zscaler, you can find the ZSAService folder. By modifying said folder, ZScaler will not be able to function, de facto disabling its protection.
When Zscaler is not running, it is possible to remove the Agent via the following process:
Control Panel > Programs and Functionalities > Zscaler > Uninstall/Change
At this point, the Tamper Protection password is required:
However, since the ZScaler Client does not retrieve anymore the ZSAService.exe, that was available in the ZSAService folder, it will just be sufficient to press OK, close the window or just insert whatever word in the field needed to actuate the removal.
The same result can be obtained even by changing the name of ZSAService.exe.